Packet filtering allows you to control access to network regardless of which program initiates connection. Dr.Web Firewall applies these rules to network packets transmitted through network interfaces of your computer.
Packet filtering allows you to control access to networks on a lower level than the application filter thus providing you with more flexible options.
Dr.Web Firewall provides you the following default filtering rule sets:
| • | Allow All – this rule set configures Dr.Web Firewall to pass through all packets. |
| • | Deny All – this rule set configures Dr.Web Firewall to block all packets. |
| • | Default Rule – this set includes rules describing the most popular system configurations and preventing common network attacks. This rule set is used by default for new network interfaces. |
For fast switching between filtering modes, you can create custom sets of filtering rules.
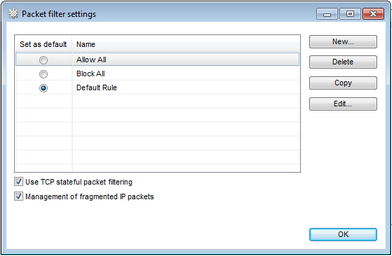
For details on a certain option, click a corresponding item in the picture.
To set rule sets for network interfaces
In the Dr.Web Firewall settings window, select Packet filter section. On this page you can:
| • | Configure sets of filtering rules by adding new rules, modifying or deleting existing ones, or changing order of rules execution. |
| • | Configure general filtering settings. |
To configure sets of filtering rules
Do one of the following:
| • | to add a new set of rules, click New. |
| • | to edit an existing set of rules, select the rule set in the list and click Edit. |
| • | to add a copy of existing set of rules, select the rule set and click Copy. The copy is added after the selected rule set. |
| • | to delete a selected rule set, click Delete. |
On the Packet Filter settings, use the following options:
Option |
Description |
|---|---|
Use TCP stateful packet filtering |
Select this checkbox to filter packets according to the state of existing TCP connections. Dr.Web Firewall will block packets that do not match active connections according to the TCP protocol specification. This option helps protect your computer from DoS attacks (denial of service), resource scanning, data injection and other malicious operations. It is also recommended to enable stateful packet filtering when using complex data transfer protocols such as FTP, SIP, etc. Clear this checkbox to filter packets without regard to state of TCP sessions. |
Management of fragmented IP packets |
Select this checkbox to ensure correct processing of large amounts of data. The maximum transmission unit (MTU) may vary for different networks, therefore large IP packets may be received fragmented. When this option is enabled, Dr.Web Firewall applies the rule selected for the first fragment of a large IP packet to all other fragments. Clear this checkbox to process fragmented packets independently. |