To access the Scanner settings, you are prompted to enter the password if you enabled the Protect Dr.Web settings with a password option in the Settings window. |
The default settings are optimal for most cases. Do not change them unnecessarily.
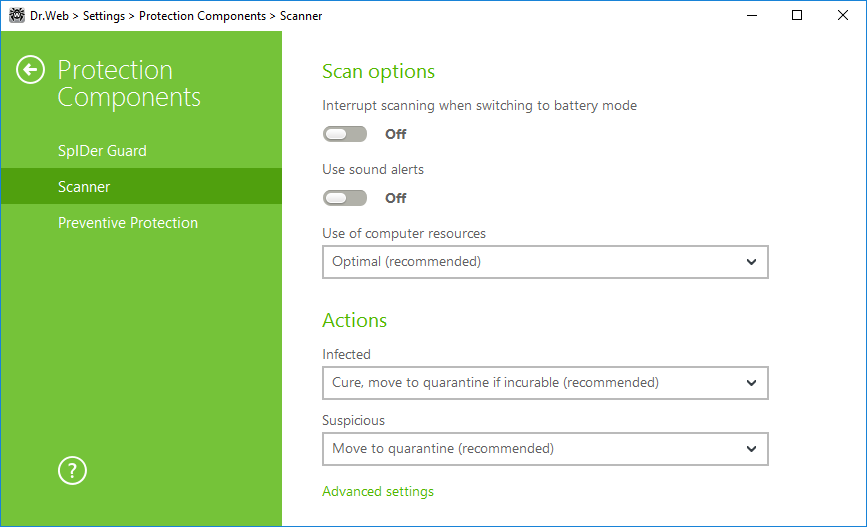
Figure 30. Scanner settings
Scan options
In this group, you can configure general parameters of Dr.Web Scanner operation.
•Interrupt scanning when switching to battery mode. Enable this option to interrupt scanning when switching to battery mode. Option is disabled by default.
•Use sound alerts. Enable this option for Dr.Web Scanner to use sound alerts for every event. Option is disabled by default.
•Use of computer resources. This option limits the use of computer resources by Dr.Web Scanner. The default value is optimal for most cases.
Actions
On this page, you can configure reaction of Scanner on detection of infected or suspicious files and archives or other malicious objects.
For different types of compromised objects, actions are assigned separately from the respective drop-down lists:
•Infected—objects infected with a known and (supposedly) curable virus.
•Suspicious—objects supposedly infected with a virus or containing a malicious object.
•Objects that pose potential threat (riskware).
Reaction of Scanner to detection of various malicious software is also set separately. Set of actions available for the selection depends on the threat type.
By default, Scanner attempts to cure the infected and supposedly curable files, moves other most dangerous objects to Quarantine.![]() Details
Details
You can select one of the following actions for detected threats:
|
Threats within complex objects (archives, email attachments, file containers) cannot be processed individually. For such threats, Dr.Web Scanner applies an action selected for this type of a complex object. |
Advanced settings
You can disable check of installation packages, archives, and email files. This option is enabled by default.
You can also select one of the following actions for Scanner to perform once scanning is complete:
1.Do not apply action. Scanner will display the list of detected threats.
2.Neutralize detected threats. Scanner will neutralize threats automatically.
3.Neutralize detected threats and shut down computer. Scanner will shut down the computer once threats are automatically neutralized.