By default, SpIDer Mail intercepts e-mail traffic of all applications running on your computer automatically. On this page, you can configure interception of connections between mail clients and mail servers, as well as list applications whose mail traffic you want to exclude from monitoring with SpIDer Mail.
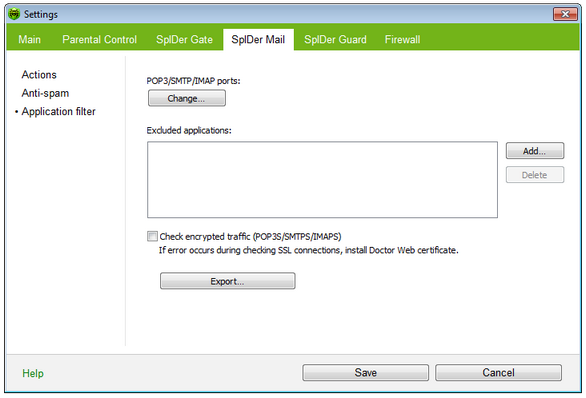
For details on a certain option, click a corresponding item in the picture.
To get information on options available in other pages, click the corresponding link in the picture.
Connection Interception
SpIDer Mail supports POP3, SMTP, IMAP4, and NNTP mail server and intercepts connections in both modes:
| • | Automatic, when interception is transparent for the mail programs. This mode is optimal for most uses. You do not need to configure mail programs to support this mode. |
| • | Manual, when SpIDer Mail serves as an explicitly defined proxy server between mail programs and servers. To use this mode, you need to configure mail programs. |
In automatic mode, SpIDer Mail intercepts connections to any supported mail server regardless of the server IP address. It is not recommended to add rules for the manual interception unless one or more of the monitored mail clients are not supported in the automatic mode.
To configure interception options for a mode, click Change under the list of ports.
Exceptions List
By default, the list is empty. You can add applications to the list.
To list exclusions
| 1. | Do one of the following: |
| • | Click Browse and select the application executable. |
| • | Enter the fill path to the application executable. |
| 2. | Click Add. |
| 3. | To add other applications to the list, repeat steps 1 to 2. To remove an application from the list and resume monitoring its e-mail messages with SpIDer Mail, select the corresponding item and click Delete. |
Secure Connections
You can enable scanning of data transmitted via secure protocols such as POP3S, SMTPS, IMAPS. To check such data, select the Check encrypted traffic (POP3S/SMTPS/IMAPS) checkbox. If your client application that uses secure connections does not refer to the default Windows system certificate storage, then you need to export Doctor Web SSL certificate.
Doctor Web Certificate
You may need to scan data transmitted in accordance with SSL protocol. For instance, you can set SpIDer Gate to check encrypted data transmitted via HTTPS protocol, or set SpIDer Mail to receive and send messages via POP3S, SMTPS, or IMAPS. These protocols use encrypted SSL connections. In order for Dr.Web to scan such encrypted traffic and maintain transparent integration with some browsers and mail clients that do not refer to the Windows system certificate storage, it may be necessary to import Doctor Web SSL certificate into the application certificate storages. To save the certificate from the system storage for future use in third party applications, click Export and select a convenient folder.