The Monitor scans all incoming and outgoing messages in real-time mode as they are processed by the Lotus Domino server. Its operation parameters can be configured for different profiles to suit the needs of various groups of clients (see Groups and Profiles).
To configure parameters of the Monitor operation
1.Select the profile in the hierarchical menu and open the Monitor subsection.
By default, the heuristic analyzer and scanning of archives in attachments are enabled. This ensures a high level of protection at the expense of the server computational resources. To disable these features, clear the Enable heuristic analysis and Check archives check boxes at the top of the Monitor frame.
It is not recommended that you disable the heuristic analyzer and scanning of archives in attachments as it greatly decreases the protection level of the server. |
2.In the Malware group of settings, you can choose actions for various types of potentially malicious programs. In the Action group of settings, you can choose actions for incurable, suspicious, and objects that cannot be scanned. For that, use the corresponding drop-down lists:
•Delete attachment—the message body will be skipped and delivered to the receiver and the attachment will be replaced by a text file with the time of detection, information on the detected virus and performed action (available for suspicious, incurable objects, and malware only).
•Quarantine attachment—the message body will be skipped and the attachment will be sent to the Quarantine database (see Managing Quarantine). A text file with the time of detection, information on the detected virus and performed action is attached to the email.
•Skip—the message body and attachments will be delivered to the receiver without any actions applied (available for objects that cannot be scanned and malware).
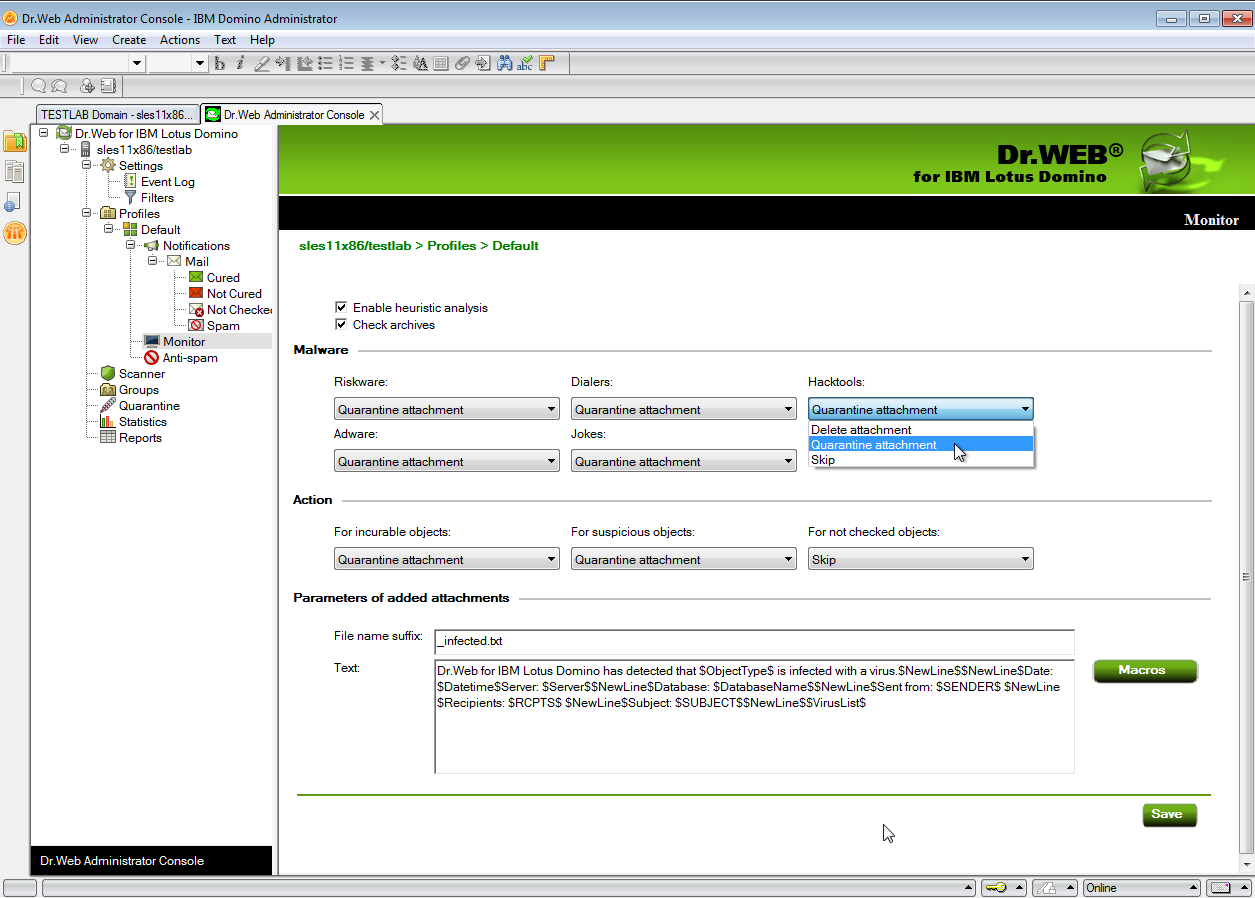
Monitor frame. Selecting actions for malicious programs
3.In the Parameters of added attachments group of settings, you can change the suffix of the name of the text file attached to an infected email message when an action is applied to it (that is, the new file name will consist of the original name with the suffix added at the end). In the Text field, you can edit the text of the attached text file if necessary.
4.To add a new macro to the text file template, click the Macros button and select the necessary macro from the list.
5.When you finish configuring the Monitor operation parameters, click Save.