Before anti-spam scanning starts, the addresses of the recipients and senders are analyzed against the black and white lists, which are specified on the Anti-spam section. Then the Anti-spam component checks the message.
The Anti-spam component analyzes the contents of messages and determines whether it is spam or not according to the spam-rate value summed up from various criteria. Depending on the analysis result, Anti-spam assigns an integer number (score) to the message. A large number means that the message is likely to be spam. You can change the threshold value that is used to detect if the message is spam in Dr.Web CMS Web Console.
|
Please forward false positive to nonspam@drweb.com and skipped spam to spam@drweb.com. |
Anti-spam is configured in the Anti-spam section of the profile settings and it is available only with the Anti-Virus&Anti-Spam version of Dr.Web. If your key file supports the Anti-spam component then spam filtering should be enabled by default, i.e., the Enable Anti-spam check box at the top of the Anti-Spam pane should be selected.
|
If all the settings in the Anti-spam section are disabled, it is likely that your license key file does not support the Anti-spam component . To check whether the Anti-spam component is supported, you can open the key file (%PROGRAMFILES%\DrWeb for Exchange\drweb32.key) with a text editor and check the value of the parameter SpamFilter. If SpamFilter=Yes, then your license supports the Anti-spam component, if SpamFilter=No, then this component is not supported. Any editing of the key file makes it invalid! Do not save the file when closing the text editor. |
To configure the Anti-spam component settings
1.Click Anti-spam in the Dr.Web Administrator Web Console console tree. The Anti-spam settings pane will open (see Figure 4).
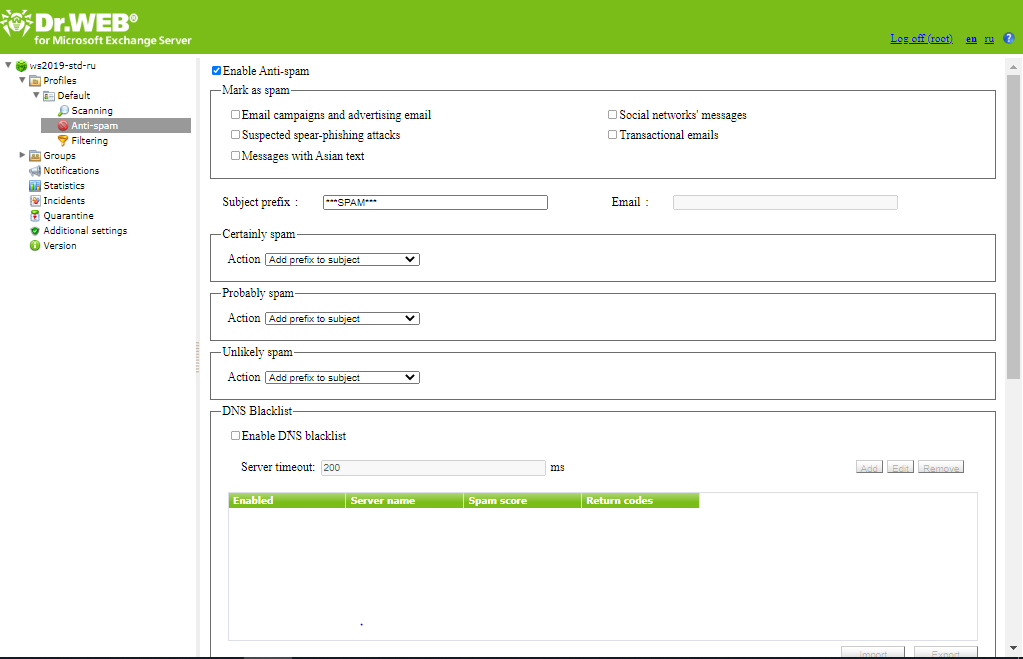
Figure 4. Anti-spam settings pane
2.To disable spam filtering, clear the Enable anti-spam check box. Once the check box is cleared, all parameters become unavailable for editing. Select the check box to enable spam filtering.
3.In the Mark as spam section you can select additional objects that will be also marked as spam.
•Еmail campaigns and advertising email—commercial emails (advertising campaigns, notifications about special offers and sales, etc.).
•Suspected spear-phishing attacks—messages that are sent to a specific company or its employee in order to get confidential data.
•Social networks' messages—social networks' notifications.
•Transactional emails—messages that are sent during account registration, purchasing goods or services, bank statements, etc.
•Messages with Asian text—messages with the most spread Asian encodings. If the check box is cleared, such emails are not marked as spam without prior analysis.
4.In the Subject prefix field, you can change the prefix, which will be added to the subjects of email messages considered as spam. The default prefix is *** SPAM ***.
5.In the Email field, enter the email address you can specify the email address to redirect the spam messages.
6.In the fields below, you can define the program actions for three categories of messages based on the probability level of their being spam (Certainly spam, Probably spam or Unlikely spam). To do this, select one of the following actions for each category:
•Add prefix to subject. The prefix defined in the Subject prefix field will be added to the message subject.
•Ignore. The message will be passed through to the recipient.
•Mark with Move to junk stamp. The X-MS-Exchange-Organization-SCL header is added to the message, together with the message distrust index score. If the score is between 4 and 7, properly configured clients will move such message to the junk folder.
•Redirect. The message will be redirected to the address specified in the Email field.
•Block. Message sending will be blocked.
7.In the DNS Blacklist section, you can configure checking against DNSBL. The client IP address, from which the server receives message, is checked against this black lists.
8.In the Black and white lists section, you can configure the use of the lists of trusted and distrusted addresses:
•Select the Enable black and white lists check box to enable the use of the lists. You can add email addresses you trust to the white list. White lists do not apply to email addresses with Unlikely spam status. If you add an address to the black list, all messages from it will be considered as Certainly spam.
•To add an address to the list, enter it in the Email field and click Add on the section of the white or black list. The address will be added to the selected list.
•To delete an address from the list, select it and click Remove on the section of the list this address is included in.
•You can also use the Export and Import buttons to save the list into a special file with .lst extension or to load the lists from the file and to create or edit the lists manually using a text editor, for example while creating and/or editing the files of black and white lists manually, you need to add prefix to the emails: "+" to add the email into the white list, "-" to add the email into the black list, e.g., +trusted_address@mail.com and -distrusted_address@mail.com. The created text file must be saved with .lst extension in Unicode format.
|
You can use the asterisk ("*") to substitute a part of the address (e.g., *@domain.org stands for any address in the domain.org domain).
In some cases adding a domain to the white list as described above might not work. To exclude this domain from spam check definitively, add it to the values list of the TrustedDomains variable. |
9.In the Dump of spam emails section, you can configure the dump of emails that were identified as spam:
•Select the Enable dump of spam emails check box to enable dumping of spam emails.
•To specify a folder to export dumps of spam emails, click Browse. Dumps of spam emails will be stored in special files with .txt extension.
•If you need to empty the folder with dumps of spam emails, click Empty dump folder. The contents of folder will be deleted.
10. In the Dump of non-spam emails section, you can configure the dump of emails that were identified as not a spam:
•Select the Enable dump of non-spam emails check box to enable dumping of non-spam emails.
•To specify a folder to export dumps of non-spam emails, click Browse. Dumps of non-spam emails will be stored in special files with .txt extension.
•If you need to empty the folder with dumps of non-spam emails, click Empty dump folder. The contents of folder will be deleted.
11. When you finish setting up the Anti-spam component, click Save.
1.In the DNS Blacklist section, select the Enable DNS blacklist check box.

Figure 5. DNSBL configuring section
2.In the Server timeout field, specify general request timeout for all the selected DNSBL servers. If the timeout has expired during an address checking, the checking is stopped and only responses already received are considered. The default value is 200 ms. You can change this value if needed.
3.The table below shows the list of servers added to DNS blacklist. Select check boxes corresponding to the server names in the Enabled column to enable sending requests to these servers. The requests are sent to all the selected servers at once.
4.Using the Add, Edit and Remove buttons, you can edit the black list and configure DNSBL server settings.
5.To export the DNSBL with server settings, click Export. The data on the servers will be exported to a .txt file. You can, for example, import this file to the Dr.Web on another mail server.
6.Using the Import button, you can import the DNSBL with server settings from previously saved file.
7.Click Save to save the settings.
To add a new server to the list
1.In the DNS Blacklist section (see Figure 5), click Add.
2.In the Add server window, fill in the Server name field.
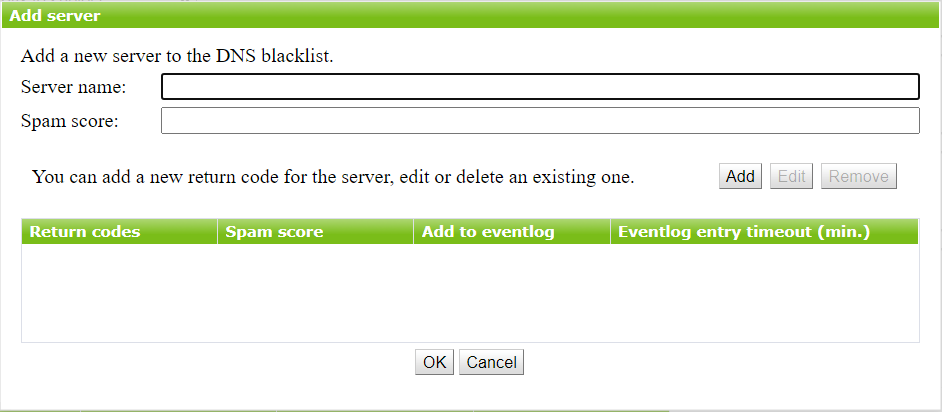
Figure 6. Adding server to DNSBL window
3.In the Spam score field, specify the score that will be assigned for the message sender's IP address match with DNSBL entry (hereinafter referred to as server overall spam score).
4.To save the data entered, click OK.
The settings of the new server will be displayed in the DNSBL table.
To change DNSBL server settings
1.In the DNS Blacklist section (see Figure 5), select a row with the server name and click Edit.
2.Change the settings in the Edit server window.
3.To save the data entered, click OK.
The new settings of the server will be displayed in the DNSBL table.
To delete a server from DNSBL
1.In the DNS Blacklist section (see Figure 5), select a row with the server name and click Remove.
2.In the open window, confirm removing the selected server from the list.
In the Add server and Edit server windows, you can also add a new return code for the server, edit or delete an existing return code.
|
If return codes are not specified, when the IP address of a message sender matches the DNSBL entry, the server overall spam score will be added to the total score sum. If you have configured a list of return codes, and a code from this list is received in response, the spam score specified for this return code will be added to the total score sum. If you have configured a list of return codes, and you receive in response a return code that is not in the list (including special error return code), for all such codes the server overall spam score will be added to the total score sum once. |
To add a new return code for the selected DNSBL server
1.In the Add server window (see Figure 6), click Add.
The Add return code window opens.

Figure 7. Adding return code window
2.Enter a value in the Return code field.
3.In the Spam score field, specify the spam score that will be assigned when this return code is matched.
4.To log the entry with this return code to the Event log, select Yes in the Add to eventlog option.
|
To view the log entries, use Event Viewer, the Windows standard component. Select the Applications and Services Log section and open Doctor Web log. Among other application events, there will be warnings with responses from DNSBL servers. See also View Incidents section. |
5.Then specify the minimum time interval between two log entries. Enter a time value (in minutes) in the Eventlog entry timeout field.
6.To save the data entered, click OK.
The settings of the new return code will be displayed in the table with the list of return codes.
To change the settings of an existing return code
1.In the Add/Edit window (see Figure 6), select a row with the return code and click Edit.
2.Change the settings in the Edit return code window.
3.To save the data entered, click OK.
The new settings of the return code will be displayed in the table.
To remove an existing return code
1.In the Add/Edit window (see Figure 6), select a row with the return code and click Delete.
2.In the open window, confirm deleting the selected return code.