On this page, you can select a mode to scan files and processes on the protected computer. You can also enable background scanning of your operating system for rootkits , i.e. malicious programs that are used for hiding changes to the operating system such as running of particular processes, registry changes, modifications to files and folders.
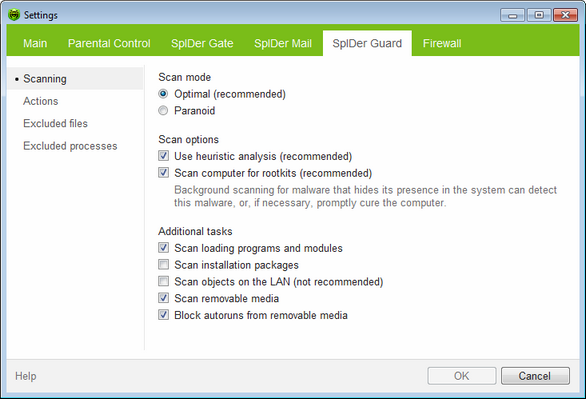
For details on a certain option, click the corresponding item in the picture.
To get information on options available on other pages, click the corresponding item in the picture.
Element |
Description |
|---|---|
Optimal (recommended) |
Scan only created or changed files on fixed disks (hard drive partitions of the PC) and all open files on removable media (diskettes, compact disks) or network drives, as well as scan files of processes being run. Thus, files on fixed disks are checked only once, when they are created (or changed). |
Paranoid |
Use other scanning settings, different from the ones of Optimal mode. |
Use heuristic analysis (recommended) |
Select to use heuristic analyzer when scanning objects "on the fly". Clear to use signature analysis only. |
Scan computer for rootkits (recommended) |
Select to enable background scanning for rootkits. |
Scan loading programs and modules |
Select to check programs and modules while they are loading regardless of their location. |
Scan install packages |
Select to scan installation packages. |
Scan objects on the LAN (not recommended) |
Select to scan files on network drives when opening or launching these files. |
Scan the removable media |
Select to scan files on removable storages (CD and DVD disks, floppy disks (FDD), flash drives and other data carriers connectable through USB, etc.) at any attempt to access such files, including opening of read-only files. |
Block autoruns from removable media |
Select to disable the autoplay option for portable data storages such as CD/DVD, flash memory, and so on. This option helps to protect you computer from viruses transmitted via removable media. |
Scan Mode
In this group, you can set up what actions with objects require scanning "on-the-fly" with SpIDer Guard.
Option |
Description |
|---|---|
This scan mode is used by default. In this mode, SpIDer Guard scans objects only when one of the following actions is traced: •For objects on hard drives, an attempt to execute a file, create a new file or add a record to an existing file or boot sector. •For objects on removable devices, an attempt to access file or boot sectors in any way (write, read, execute). |
|
Paranoid |
In this mode, SpIDer Guard scans files and boot sectors on hard or network drives and portable data storages at any attempt to access them (create, write, read, execute). |
|
When running in the Optimal mode, SpIDer Guard does not terminate execution of an EICAR test file and the file is not processed as malicious since it does not pose any actual threat to your system. However, if you copy or create such a file in your system, it will be detected by SpIDer Guard and moved to Quarantine by default. |
The Optimal mode is recommended for use after a thorough scan of all hard drives by Dr.Web Scanner. With this mode activated, SpIDer Guard prevents penetration of new viruses and other malicious objects via removable devices into your computer while preserving performance by omitting knowingly "clean" objects from repeated scans. The Paranoid mode ensures maximum protection, but considerably reduces computer performance. In any mode, objects on removable media and network drives are scanned only if the corresponding check boxes in the Additional tasks group are selected. On the Actions page, you can configure reaction of SpIDer Guard on detection of malicious objects.
|
Background Rootkit Scanning
Anti-rootkitcomponent included in Dr.Web provides options for background scanning of the operating system for complex threats and curing of detected active infections when necessary.
If this option is enabled, Dr.Web Anti-rootkit constantly resides in memory. In contrast to on-the-fly scanning of files by SpIDer Guard, scanning for rootkits , i.e. malicious programs that are used for hiding changes to operating system such as running of particular processes, registry changes, modifications to files and folders, includes checking of autorun objects, running processes and modules, Random Access Memory (RAM), MBR/VBR disks, computer BIOS system and other system objects.
One of the key features of the Dr.Web Anti-rootkit is delicate attitude towards consumption of system resources (processor time, free RAM and others) as well as consideration of hardware capacity.
When Dr.Web Anti-rootkit detects a threat, it notifies you on that and neutralizes the malicious activity.
|
During background rootkit scanning, files and folders specified on Excluded files page of SpIDer Guard are excluded from scanning. |
To enable background scanning, set the Scan computer for rootkits (recommended) check box.
|
Disabling of SpIDer Guard does not affect background scanning. If the check box is set, background scanning is performed regardless of whether SpIDer Guard is enabled or disabled. |
Additional Tasks
The settings of this group allow to specify parameters for scanning objects "on-the-fly" and are always applied regardless of the selected SpIDer Guard operation mode. You can also select Block autoruns from removable media check box to disable autoplay option for portable data storages such as CD/DVD, flash memory, and so on.This option helps to protect you computer from viruses transmitted via removable media.
In this group, you can configure SpIDer Guard parameters to check the following objects:
•Executables of running processes regardless of their location
•Installation files
•Files on network drives
•Files and boot sectors on removable devices
|
If any problem occur during installation with autorun option, it is recommended to clear Block autoruns from removable media check box. |
See also: