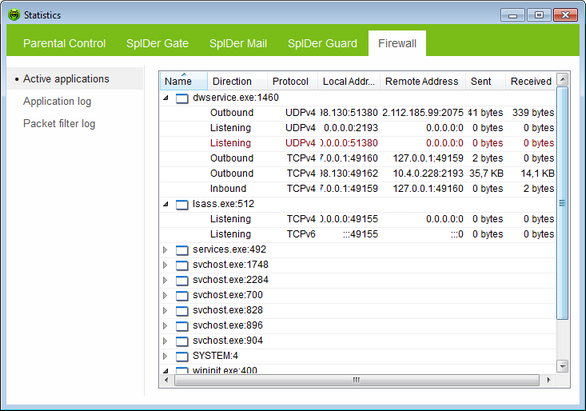
The list of active applications displays information on programs that are currently accessing network resources.
For details on a certain option, click the corresponding item in the picture.
To get information on options available on other pages, click the corresponding item in the picture.
For each application, the following information on active connections is available:
Column |
Description |
|---|---|
Name |
The name of the application. |
Direction |
The direction of the connection: •Inbound – the rule is applied when someone from the network attempts to connect to an application on your computer. •Outbound – the rule is applied when an application on your computer attempts to connect to the network. •Listening – the rule is applied when the application on your computer is waiting for a connection attempt from the network. |
Protocol |
The protocol used to transmit data. |
Local address |
The protocol and host address from which comes an attempt to connect. |
Endpoint |
The used protocol and network address to which the application is trying to connect. |
Sent |
The number of bytes sent through this connection. |
Received |
The number of bytes received through this connection. |
In the window with statistics on active applications, you can terminate any active process by right-clicking the process in the table and selecting Terminate process.
|
To terminate an active process, administrative privileges are required. Otherwise, you can terminate only those processes that are run under your account. |
From the shortcut menu you can also block an active or unblock a disabled connection. Blocked connections are marked with red font in the table.