Application filtering rules control interaction of a particular application with certain network hosts.
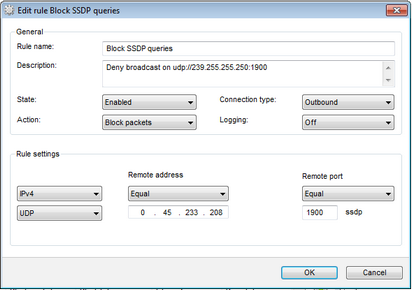
For details on a certain option, click a corresponding item in the picture.
To add or edit a rule
| 1. | Configure the following parameters: |
Parameter |
Description |
||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
General |
|||||||||||||
Rule name |
The rule name. |
||||||||||||
Description |
The rule description. |
||||||||||||
State |
One of the following execution states for the rule:
|
||||||||||||
Connection type |
The party which initiates the connection:
|
||||||||||||
Action |
The action for Dr.Web Firewall to perform when the connection attempt is detected:
|
||||||||||||
Rule Settings |
|||||||||||||
Protocol |
The network and transport level protocols used for the connection attempt. Dr.Web Firewall supports the following network level protocols:
Dr.Web Firewall supports the following transport level protocols:
|
||||||||||||
Inbound/Outbound address |
The IP address of the remote host. You can specify either a specific address (Equals) or several IP addresses using a range (In range), specific subnetwork mask (Mask), or masks of all subnetworks, in which your computer has network addresses (MY_NETWORK). To apply the rule for all remote hosts, select Any. |
||||||||||||
Inbound/Outbound port |
The port used for connection. You can specify either a specific port number (Equals) or a port range (In range). To apply the rule for all ports, select Any. |
||||||||||||
2. When you finish adjusting the settings, click OK to save changes or Cancel to reject them.