|
There are two ways the component can protect emails:
1.Connection to the mail server (Sendmail, Postfix, Exim, etc.) as an external email filter (using any of the following extensions: Milter, Spamd, Rspamd, supported by the mail server). 2.Setting up proxy that performs scanning of emails transferred via SMTP, POP3 or IMAP4 protocols transparently for the mail server. To set up this scanning method, SpIDer Gate and Dr.Web Firewall for Linux are used. As these components operate only with GNU/Linux, this method is available only for this family of operating systems. Checked email messages are processed according to the rules set in the component settings. For each interface used for interaction with mail servers, its own rule system for email message processing can be determined. In case of usage of the proxy mechanism (i.e. during the scanning of email messages received directly via the protocols SMTP, POP3, IMAP), the component uses the processing rules determined in the settings of Dr.Web Firewall for Linux.
Scanning of URLs in email messages uses the same automatically updated databases of web resource categories as SpIDer Gate. Dr.Web CloudD component is used to refer to Dr.Web Cloud cloud service (using of the cloud service is configured in Appendixes common settings and can be disabled, if necessary). To check transferred data, Dr.Web MailD uses the Dr.Web Network Checker component. The latter one initiates scanning via the Dr.Web Scanning Engine scanning engine.
Depending on the conditions (email message characteristics, triggered rules and a protocol that brought the email message to scanning by the component), the component could execute the following actions regarding the email:
Action
|
Description
|
Pass
(Pass)
|
The email message will be delivered to the recipient. Besides, all actions aimed at adding and changing headers will be applied, as well as actions aimed at repacking if such have been indicated in the rules triggered for this email message.
Arguments: None.
Features of action implementation:
An action can be applied for all methods of connection to MTA, as well as for integration via the proxy mechanism into any mail protocol.
|
Reject
(Reject)
|
The email message will not be accepted from the sender (for POP3/IMAP—from the mail server) and will not be delivered to the recipient.
Features of action implementation:
•Integration with MTA as a filter: For interfaces Spamd and Rspamd MTA returns the verdict “the email message is spam”. Real action with the email message depends on the settings of the protected MTA. Optional parameter of the action <description>, if indicated, will be used as the value of the header “Message”, added by MTA to the email message after the message with scanning results (it allows to indirectly return to MTA the reason of the email message rejection).
•Integration into mail protocols via the proxy mechanism: ▫For protocols IMAP and POP3, return email messages to the sender, i.e. MUA, protocol error. ▫For SMTP—return of the code 541 to the sender. |
Temporary error
(Tempfail)
|
The email message will not be accepted from the sender (for POP3/IMAP—from the mail server) and will not be delivered to the recipient.
Features of action implementation:
•Integration with MTA as a filter: For interfaces Spamd and Rspamd MTA returns the verdict “the email message is spam”. Real action with the email message depends on the settings of the protected MTA. Optional parameter of the action <description>, if indicated, will be used as the value of the header “Message”, added by MTA to the email message after the message with scanning results (it allows to indirectly return to MTA the reason of the email message rejection).
•Integration into mail protocols via the proxy mechanism: ▫For protocols IMAP and POP3, return email messages to the sender, i.e. MUA, protocol error. ▫For SMTP—return of the code 451 to the sender. |
Discard
(Discard)
|
The email message will not be accepted from the sender (for POP3/IMAP—from the mail server) and will not be delivered to the recipient.
Features of action implementation:
•Integration with MTA as a filter: For interfaces Spamd and Rspamd MTA returns the verdict “the email message is spam”. Real action with the email message depends on the settings of the protected MTA.
•Integration into mail protocols via the proxy mechanism: ▫For protocols IMAP and POP3, return email messages to the sender, i.e. MUA, protocol error. ▫For SMTP—receipt of the email message from the sender with the OK confirmation and removal instead of delivery to the recipient. |
Block
(Block)
|
Synonym for the action “Reject”. Used for compatibility.
|
Repack
(Repack)
|
The email message will be delivered to the recipient changed: it will have an added notification on detection of threats, and the threats themselves will be placed in the archive attached to the created email message. Depending on the settings, this archive can be protected with password.
If threats were in headers or text of the email message, not in its attachments (including cases when the email letter is considered spam or does not meet the corresponding security policy determined by the administrator in the rules), all source email message will be entirely placed in the source email message.
There are the following predetermined templates for repacking:
1.The email message is spam (the source email message is moved to the archive); 2.One or more threats in the email message (files with threats are moved to the archive); 3.One or more malicious/unwanted URLs in the email message (the source email message or its parts containing URL are moved to the archive); 4.Violation of the security policy established by the administrator (the source email message or its unwanted parts are moved to the archive). The action will be applied to the email message if the rules contain the final resolution Pass (or does not contain Reject, Block, Tempfail, Discard).
Features of action implementation:
•Integration with MTA as a filter: For interfaces Spamd and Rspamd it is not supported (impossible to return the server the modified email message).
|
Add header
(Add Header)
|
Add the indicated header to the email message.
The action will be applied to the email message if the rules contain the final resolution Pass (or does not contain Reject, Block, Tempfail, Discard).
Features of action implementation:
•Integration with MTA as a filter: For interfaces Spamd and Rspamd it is not supported (impossible to return the server the modified email message).
|
Change header
(Change Header)
|
Change value of the indicated header in the email message.
The action will be applied to the email message if the rules contain the final resolution Pass (or does not contain Reject, Block, Tempfail, Discard).
Features of action implementation:
•Integration with MTA as a filter: For interfaces Spamd and Rspamd it is not supported (impossible to return the server the modified email message).
|
For the indication of actions in rules, refer to chapter Rules for Traffic Monitoring in Appendix D. Configuration File.

|
If interaction of Dr.Web MailD with MTA uses the Spamd or Rspamd interface, the only possible action for Dr.Web MailD within this interaction is to inform MTA whether the email message is clean or classified as spam. If the email message violates any limit set by the rules, or if there is any threat in the email message, the following verdict is sent to MTA “The email message is spam”. All actions aimed at processing the email message (for example, adding headers, rejection of the email message, delivery to the recipient, etc.) must be defined in the settings on the part of MTA. Also, in this case Dr.Web MailD does not have a possibility to return the modified email message to MTA, so such actions as REPACK (“repacking” of the email message by removing malicious attachments and adding a notification on threat detection) are also impossible. To return to MTA the reasons of the email message rejection, use the action REJECT <description>. The indicated parameter <description> will be used as a value of the header “Message” added by MTA to the email message after the message with the scanning results.
|
The diagram of the components’ operation is given below.
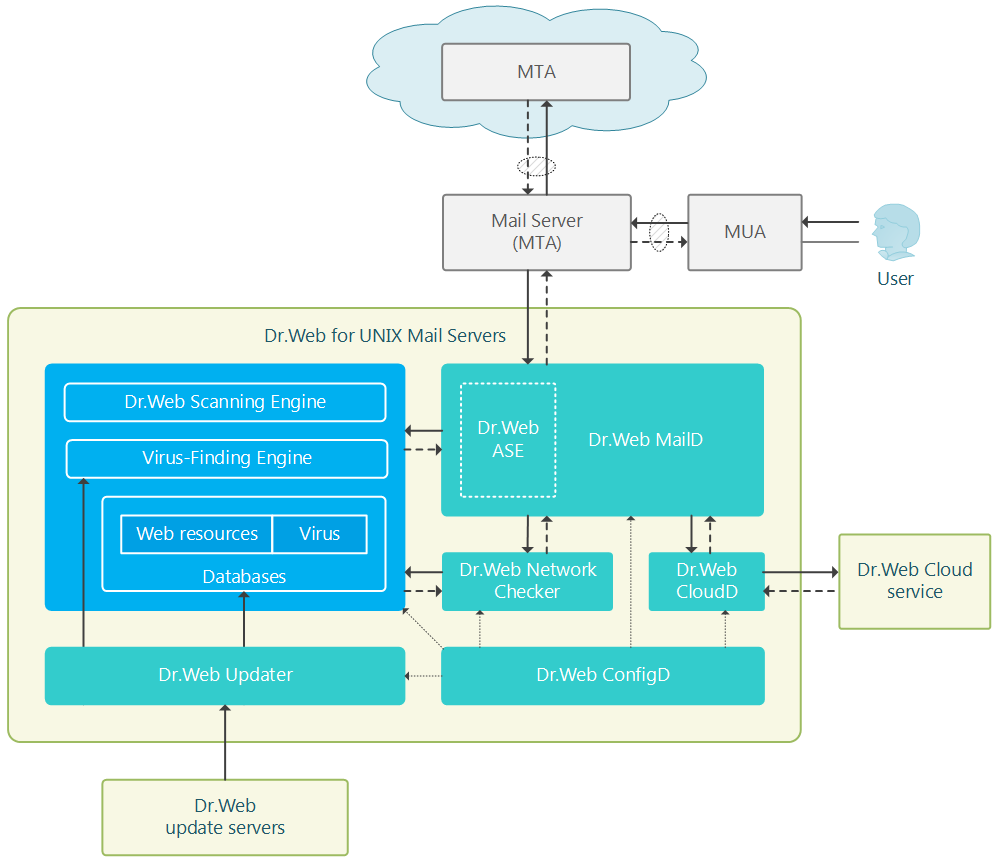
Figure 13. Diagram of the components’ operation
Hatched ellipses on the scheme are points where Dr.Web MailD can be embedded via the transparent proxy mechanism using SpIDer Gate.
For messages analysis on presence of signs Dr.Web MailD uses the special component Dr.Web ASE (Dr.Web Anti-Spam Engine).

|
Dr.Web ASE could be unavailable depending on the distribution. In this case email message scanning for signs of spam is not performed.
|
|





