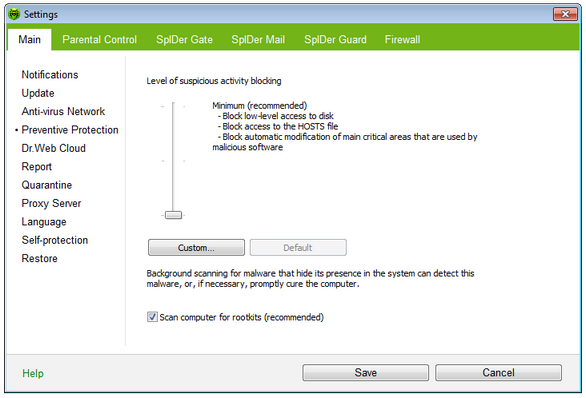
On this page, you can configure Dr.Web reaction to such actions of other programs that can compromise security of your computer. You can also enable background scanning of your operating system for rootkits , i.e. malicious programs that are used for hiding changes to operating system such as running of particular processes, registry changes, modifications to files and folders.
For details on a certain option, click a corresponding item in the picture.
To get information on options available in other pages, click the corresponding link in the picture.
Preventive Protection Level
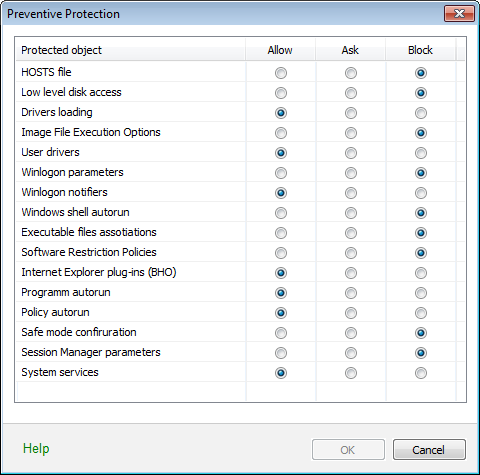
In the default Minimum mode, Dr.Web disables automatic changes to system objects, modification of which explicitly signifies a malicious attempt to damage the operating system. It also blocks low-level access to disk and protects the HOSTS file from modification. ![]() Details
Details
|
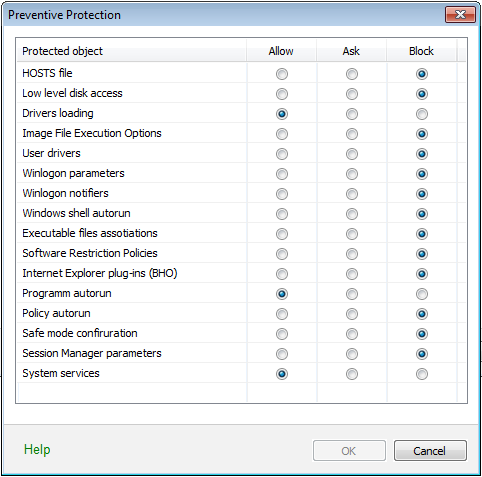
If there is a high risk of you computer getting infected, you can increase protection by selecting the Medium mode. In this mode, Dr.Web blocks access to the critical objects that can be potentially used by malicious software. ![]() Details
Details
|
|
Using this mode may lead to compatibility problems with legitimate software that uses the protected registry branches. |
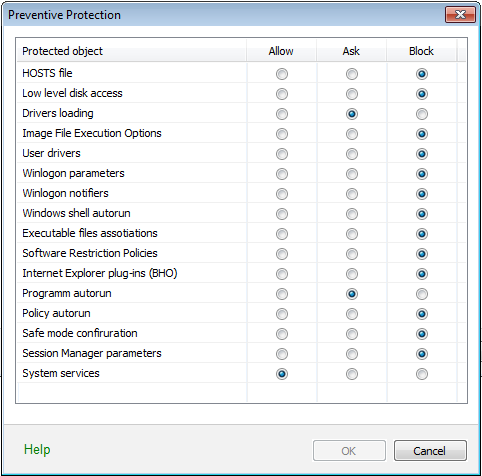
When it is required to have total control of access to critical Windows objects, you can select the Paranoid mode. In this mode, Dr.Web also provides you with interactive control over loading of drivers and automatic running of programs.![]() Details
Details
|
Custom Mode
This mode allows flexible configuration of Dr.Web reaction to particular events that can compromise security of your computer.
Protected object |
Description |
||||||||||||||||||||||||||||||||||||||||||||||
HOSTS file |
The operating system uses the HOSTS file when connecting to the Internet. Changes to this file may indicate virus infection. |
||||||||||||||||||||||||||||||||||||||||||||||
Low level disk access |
Block applications from writing on disks by sectors avoiding the file system. |
||||||||||||||||||||||||||||||||||||||||||||||
Drivers loading |
Block applications from loading new or unknown drivers. |
||||||||||||||||||||||||||||||||||||||||||||||
Critical Windows objects |
Other options allow protection of the following registry branches from modification: File Execution Options:
User Drivers:
Winlogon registry keys:
Winlogon notifiers:
Windows registry startup keys:
Executable file associations:
Browser Helper Objects for Internet Explorer (BHO):
Autorun of programs:
Autorun of policies:
Safe mode configuration:
Session Manager parameters:
System services:
|
|
If any problems occur during installation of important Microsoft updates or installation and operation of programs (including defragmentation programs), disable the corresponding options in this group. |
Background Rootkit Scanning
Anti-rootkit component included in Dr.Web provide options for background scanning of the operating system for complex threats and curing of detected active infections when necessary.
If this option is enabled, Dr.Web Anti-rootkit constantly resides in memory. In contrast to on-the-fly scanning of files by SpIDer Guard, scanning for rootkits , i.e. malicious programs that are used for hiding changes to operating system such as running of particular processes, registry changes, modifications to files and folders, includes checking of autorun objects, running processes and modules, Random Access Memory (RAM), MBR/VBR disks, computer BIOS system and other system objects.
One of the key features of the Dr.Web Anti-rootkit is delicate attitude towards consumption of system resources (processor time, free RAM and others) as well as consideration of hardware capacity.
When Dr.Web Anti-rootkit detects a threat, it notifies you on detection and neutralizes the malicious activity.
|
During background rootkit scanning, files and folders specified on Exclusion page of SpIDer Guard are excluded from scanning. |
To enable background scanning, set the Scan computer for rootkits (recommended) checkbox.